I’m way overdue on doing a proper blog post so I thought I’d swing back into action by showing everyone some really esoteric Microsoft Windows knowledge that I picked up by accident several years ago working on a research project. Around 2010 or so, I was working on Adobe Flash cookie research with Kristinn Gudjonsson of log2timeline fame. During that research, I discovered an odd occurrence dealing with Windows date and time stamps which led me into learning about file system tunneling.
So for purposes of this blog post, you don’t need to know anything about Adobe Flash cookies. I presented on them during the CEIC 2010 Conference and end of my presentation I went into the file system tunneling aspect of what I had found. This blog post covers that portion of the presentation. The only thing you need to know for purposes of this blog post is that Adobe Flash cookies, at least back when I as doing the research on them many years ago, can be deleted and then quickly replaced with a file of the exact same name and file location as the previous one.
For purposes of this demonstration, we’re using a Adobe Flash cookie file with the name “settings.sol”. I think I was using EnCase Version 6 for making this presentation in case anyone is curious about the tool being used.
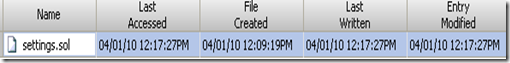
Here is our baseline “settings.sol” file before any changes are made to it.
Here is what happens when a change has been made and the original file has been deleted and replaced with a file of the exact same file name and location. I don’t have the path listed in these screenshots, but the paths of the new files of the same name are being placed in the exact same location as the old files of the same name.
Here is the brand new file with the exact same name in the exact same location:
So we are seeing what we would expect for a brand new file that was created after the old one was deleted…except look at the file creation timestamp. It exactly matches the file created timestamp of the old file that was just deleted. That’s not accurate, is it? We know the file was actually created on 04/01/10 12:17:27PM, but it’s showing the created file time of the deleted file.
Here is another way of looking at it.
Here we see the old “settings.sol” file that was deleted and we also see the new “settings.sol” file that was created in the exact same location. As you can see, the new file has last accessed, last written, and entry modified time stamps that show when it was created, but it has the wrong file created time. It kept the file creation time of the old file of the exact same name that was in the exact same location.
What on earth is going on?
This almost made me go completely insane trying to figure this out. Like any good digital forensics person, I could absolutely not let this one go and had to run it down until I had an answer. I lost track of how many digital forensics gurus that I contacted to get help. At first, I was a little reluctant to do so in case it turned out to be something obvious that I missed. Who wants to humiliate themselves with a flagrant display of ignorance in front of some digital forensics icon? I was able to save face because the responses I received were all along the lines of telling me that I had an interesting problem on my hands and they didn’t have an answer for me. The person who solved the problem in the end was Eoghan Casey. Eoghan listened to me describe what I was seeing and said he thought I might be observing file system tunneling. I did some further research and it turned out that Eoghan was exactly right.
You can find the official Microsoft write up on file system tunneling at their knowledge base 172190 article at http://support.microsoft.com/kb/172190 The relevant text (and the spelling errors are theirs) from that article is:
The Microsoft Windowsproducts listed at the beginning of this artice contain file system tunneling capabilities to enable compatibility with programs that rely on file systems being able to hold onto file meta-info for a short period of time.
When a name is removed from a directory (rename or delete), its short/long name pair and creation time are saved in a cache, keyed by the name that was removed. When a name is added to a directory (rename or create), the cache is searched to see if there is information to restore. The cache is effective per instance of a directory. If a directory is deleted, the cache for it is removed.
I haven’t performed any recent research to update this information, but at the time I was doing this research in 2010, file tunneling impacted a broad range of Microsoft operating systems including 2k, XP (including 64bit), and NT. Microsoft hasn’t updated the article since 2007, but I’d be surprised if it wasn’t an issue for Windows 7 and potentially Windows 8.
The Microsoft 172190 article goes on to explain that file system tunneling is an issue for both FAT and NTFS file systems because:
The idea is to mimic the behavior MS-DOS programs expect when they use the safe save method. They copy the modified data to a temporary file, delete the original and rename the temporary to the original. This should seem to be the original file when complete. Windows performs tunneling on both FAT and NTFS file systems to ensure long/short file names are retained when 16-bit applications perform this safe save operation.
Microsoft explains how to disable file system tunneling in the same 172190 article. All you need to do is to go to the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem setting in the registry and add a DWORD called MaximumTunnelEntries which you then set to 0.
So the Microsoft article talks about “file systems being able to hold onto file meta-info for a short period of time”. The short period of time is a default setting of fifteen seconds. However, if you wish to change that time, it’s yet another registry tweak. You just have to head over to the same key as you would to disable file system tunneling, but this time you just need to add a new DWORD called “MaximumTunnelEntryAgeInSeconds” and then whatever time you would like. This is all explained in the Microsoft 172190 article.
So like any good forensic geek, I wanted to test what I had found because I didn’t want to look foolish in front of a big audience of people at CEIC. I set up an experiment based on making Flash Cookie modifications that would initiate the same deletion and creation process. Again, all you need to know for purposes of this blog post is that I was making changes that resulted in near instant file deletion and creation of files with the exact same name in the exact same location.
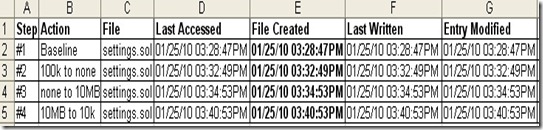
For example, I used a Windows XP SP2 system that had file system tunneling enabled and obtained these results.
I was making changes that causing these “settings.sol” files to be deleted and then replaced with files of the exact same name. Like before, we are seeing the changes that we would expect from new files being created in that their accessed, written, and modified time stamps reflect the accurate time that they were created. However, all of these new files are keeping the same file created stamp as the original file. This is file system tunneling at work.
How do we know for sure? What I did next was to follow the registry modification that I explained before to disable file system tunneling and then to run the experiment again. Again this was a Windows XP SP2 system, but with file system tunneling disabled.
Now we see that all of the file times are matching the time that the files were created including…finally… the file created times.
And because like all good digital forensics people, I’m always suspicious of what I’m seeing, I repeated the experiment a third time, but this time I used the registry to turn file system tunneling back on which resulted in...
…the exact same file system tunneling behavior that I had observed at the start of all of this.




Eric - great stuff! I bookmarked it as something that I know I'll come back to someday. One of those why does that happen again?' posts.
ReplyDeleteGood post, Eric. I've discussed this in my book, blog, and courses for some time, as it's very important for analysts to understand what actions or events create or modify various artifacts on the system. This is particularly true in timeline analysis, as this information helps provide much needed context.
ReplyDeleteI would suggest that if you were to test this on Windows 7, you would see supporting, corroborating information in the USN change journal.
Very good post, bookmarked...
ReplyDeleteEric, very interesting and a good post!
ReplyDeleteAnother excellent explanation. Thank you.
ReplyDeleteHey Eric, Question for you... Does this tunneled creation date get set when the new file is initially created, or is the correct creation time written, then changed to the old date? I'm wondering whether the filename timestamps are affected. If it's written, then changed, I'd expect the filename timestamps to reflect the actual creation time for the new file. Otherwise, they'll most likely be the same as the SIA timestamps.
ReplyDeleteThoughts? Thanks
John
These are excellent questions and I wish I remember enough about the research I did at the time to answer them. For example, I could have *sworn* I checked the $File_Name aspect of this when I ran into this issue, but I can't find any notes that I took. The rub was that at the time I was concentrating on the Adobe Flash Cookies research and this was just a roadblock in creating a presentation on my research. Yes, I would expect that the $File_Name would reflect the actual creation time, but I just can't say for sure without repeating the research.
ReplyDeleteEric-Great work thanks for introducing this problem
ReplyDelete-pramod
Hi Eric,
ReplyDeleteAfter reading your blog,I have been trying to go deeper in this concept & also doing some practical stuff on my PC to get it more clear.
I would really appreciate if you please help me following queries.
Suppose NTFS Tunneling is enabled.lets take an example say a.txt is created under ABC folder.then i deleted a.txt.(Please correct me if i am wrong ,here OS will store a.txt in its cache).
After some time i created a.txt under ABC folder.But due to NTFS tunneling is been enabled it will not reflect the correct file creation time for newly created a.txt file.
So queries are:
1.OS is storing file names only when we delete the files and
not at normal time?
2.Is there a way to access the cache of OS to search for the file name that has been deleted in this example it will be a.txt. If Yes then request you to please direct me link or answer.
Actually i want to try this & compare my observations with your given answers.
Thanks
Pramod